Basic SSH Server Security
Before I get going with installing new software on my Ubuntu unmanaged server, I want to look at some simple SSH server security in order to give some basic level protection to my server from the get-go.So the first step for my SSH server security is to remove root access. This basically then means that anyone who wishes to log on to my server will need to know (or guess) the username.
OpenSSH Add User
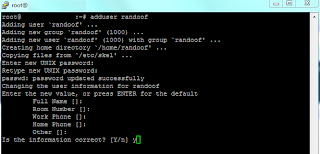
Now, you may have realised that if I remove root access then that means I will have no way to log on to my server, so obviously I will need to add another user. I will do with the the OpenSSH add user command which is, in its most simplest form "useraddHowever, I want to set up my user with a diretory, and (in some circumstances full contact details) so I will use the OpenSSH add user command "adduser
This way, the shell will create a new group, a home directory for the user and will prompt me for a password and any further information that I want to add.
As I am already logged in as the "root" user, who has maximum priveleges, I can basically do whatever I want on the server. However, when you create new users, their privileges are more limited, these can be altered which I will look at as I work through the process.
Now is probably the opportune moment to point out two points about the PuTTY terminal which Windows users (in particular) may not be familiar with. Firstly, when you enter a password in PuTTY, nothing appears, giving onlookers no idea even how many characters you have typed. Secondly, you cannot paste with ctrl+v, rather you just right click the mouse, and that will paste in whatever you have copied in your clipboard. If you wish to copy and paste in PuTTY, then select the text as normal with the mouse and then right click, and the text will be pasted at the cursor location.
So, now I have my new user "randoof" set up, with limited privleges, a home directory and a password, so the best thing to do is to "logout" and try and log back in as randoof.
Before I can disable the root user login, whenever I need to do anything with more privleges than my user has been granted, I will need to use the "sudo" command, which means "Super User do", at which point I will be prompted to enter my password.
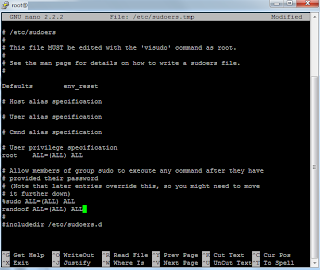
So in order to do that, I will need to log back in as root, and edit a configuration file where you can specify user priviledges.
Logged is as root, the configuration file is called by using the command "nano /etc/sudoers" and adding the line "randoof ALL=(ALL) ALL", and the ctrl+o to save the file.
The reason this is clever SSH server security, is it means that every command received is logged to a specific user, so if you have a server and 100 possible users who can access it, you can easily figure out which user completed a command. Brilliant, safe and secure.
Disable Root Access
Disable root access is the first step of our SSH server security and it is still a relatively simple process.The first step is to move to the directory which holds the SSH configuration file, from the root of the server - that is the very top directory - I will use the "cd" command (Change Directory) to navigate to the directory.
cd /etc/ssh
Out of interest, to leading slash means that you will navgate from the root of the
server first. You can always get back to the root of the directory with "cd /".
I have got into the habit of listing the files in the current directory with the "ls" command. This is purely because I am so used to navigating with a gui that I double check I am in the correct location with a list of folders and files.
Now I will use "nano", the built in text editor to edit the SSH configuration file named "sshd_config" as the root user by using the "sudo" command.
sudo nano sshd_config
Once in the file, I look for the line "PermitRootLogin yes" and simply change it to no.
Whilst I am in the sshd_config file, I am also going to change the default port. Again, this is a default setting (port 22), which hackers will know, so I am going to change this to something different by editing the line:
# What ports, IPs and protocols we listen for
Port 22
I am also going to disable X11 forwarding. X11 forwarding is used for graphical access (ie a GUI) and I won't be doing that, so it's just an extra little bit of security.
There's one final line I am going to add for that extra little bit of security and that is simple "AllowUsers randoof simon". This then limits the users who can log in to my server to Randoof and Simon. Perfect.
ctrl+o to write Out to the file (save it), followed by enter to confirm the filename and ctrl+x to exit.
Following that, the SSH server needs to be restarted, using the command
"/etc/init.d/ssh restart". If all went well, you should be informed with the line
* Restarting OpenBSD Secure Shell server sshd [ OK ]
Now if I try to login I will need to change the default port in PuTTY to my newly configured number.
An then if I try to log in as root, I am prompted for a password, and then simply "access denied".
No comments:
Post a Comment